Before being able to determine if systems are vulnerable, it’s critical to first find as many active systems within the scope as possible and to accurately determine what services those systems expose. This is generally called “Network Mapping”, and a a common tool for use in network mapping is Nmap. Nmap is famous for its port scanning capability, but is has a lot more features than just port scanning.
There’s also an Nmap book, of which about half is available online for free.
A Simple Example
Before we start looking at the many, many, options that Nmap has, we’ll take a look at a simple example. Nmap can be invoked with a target IP address and it will perform a default scan. If Nmap is invoked with administrative/root privileges it will perform a “half-open” SYN scan which is beneficial for its potential to be stealthier and faster than a “full” scan. A full-handshake scan can will be performed if administrative permissions are not granted, or optionally with the -sT flag.
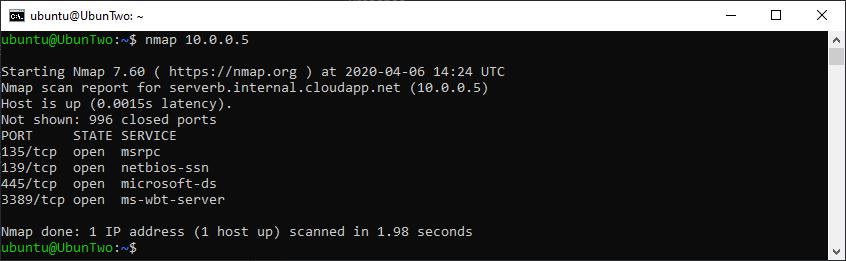
Nmap running with default options
From the above you can see key details such as when the scan started (14:24), how long it took (1.98 seconds), and which ports were open (TCP: 135, 139, 445, 3389). However it’s worth noting that with a default scan, the “Service” which is listed is simply the service which is commonly found on that port and not what is actually running. To determine what is actually running version scanning can be performed with -sV. There are several states which could be show, such as open, closed and filtered. Where open denotes a port with a running service, close denotes a port that is does not appear to be restricted by a firewall but which is not running a service currently, and filtered which denotes a firewall restriction.
Now let’s take a look at some common scan options:
Scoping
Nmap can be given multiple target IP addresses, in several different ways:
| Input | Example |
|---|---|
| Comma separated | 10.0.0.1,2,3,4 |
| Space separated | 10.0.0.1 10.0.0.2 10.0.0.3 |
| Hyphen separated | 10.0.0.1-4 |
| CIDR Notation | 10.0.0.0/28 |
| Line separated in file | -iL scope.txt |
Example usage:nmap 10.0.0.1-10Saving Output
Saving Nmap output is an important part of network mapping of course and there are several options.
| Flag | Output |
|---|---|
| -oN | Normal mode output, essentially stdout |
| -oG | Grep-able output |
| -oX | XML output |
Example usage:nmap 10.0.0.1-10 -oN output.txtSpeed
The speed Nmap speed settings can be adjusted in several ways but one of the simplest is to use “Timing Templates”. The Nmap book recommends that generally -T4 is fine to use, if you are on a “decent broadband or ethernet connection” and that -T3 is fine for “cautious scanners”. It also notes that -T2 can take ten times longer to run than -T3. The available templates are:
| Template | Name |
|---|---|
| -T0 | Paranoid |
| -T1 | Sneaky |
| -T2 | Polite |
| -T3 | Normal |
| -T4 | Aggressive |
| -T5 | Insane |
If these timing templates are not finely-grained enough, additional timing options are available such as: –osscan-limit, –max-rtt-timeout, –max-parallelism, or –min-hostgroup. Alternatively adjusting other scan options can help such as disabling DNS resolution, -n, reducing the number of ports scanned, –top-ports, or using fast scan, -F.
Example usage:nmap 10.0.0.0/24 -T5Service and Version Detection
A common thing to want to achieve is determining exactly what software the remote system is running, instead of just which ports are open. Useful options for service and version detection are:
| Flag | Detail |
|---|---|
| -p ports | Check a comma separated list of ports. |
| -p1-1024 | Check a port range. |
| -p- | Check ports 1-65535, alternatively supply -p0- to include port 0. |
| -Pn | Treat the machine as up, even if it rejects ping requests. |
| -n | Do not perform name resolution. |
| -sn | Do not port scan, just look for alive hosts. |
| -sV | Enable version scanning and attempt to determine what service is running on the remote port. |
| –version-intensity | What level of intensity to use when version scanning, the default level is 7 and there are a total of 9 intensity levels. Lower intensity ratings are commonly useful and higher intensity ratings are rarely useful. |
| -O | Enable operating system version scanning. |
Example usage:nmap 10.0.0.0/24 -O -sV --version-intensity 9Nmap Scripting Engine (NSE)
Nmap includes a scripting engine and a lot of scripts for finding common issues, such as SSL/TLS cipher issues, known vulnerabilities such as MS17-010 (or “ETERNALBLUE” if you prefer), as well as password brute-forcing for services such as FTP, SNMP, and SMB.
| Flag | Detail |
|---|---|
| -sC | Enable default script scanning, this is the equivalent of –script=default. |
| –script=scriptname | Run the specified script. |
| –script=ssl-enum-ciphers | Determine which SSL/TLS ciphers are supported by a port. |
| –script=ssl-cert | List information about the X.509 certificate of an SSL/TLS service. |
Complex Example
Example output with several options enabled:
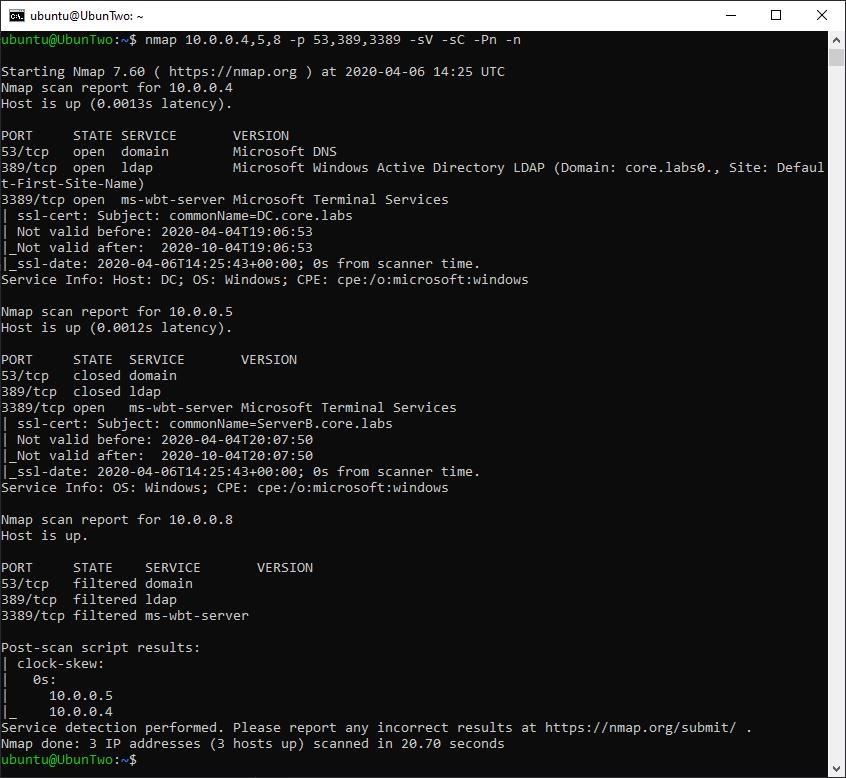
Nmap with several common options.
In the above example additional information has been gained when compared to the default scan we ran against the same device. Multiple IP addresses have been scanned instead of just an individual address (so the scan tested 10.0.0.4, 10.0.0.5 and 10.0.0.8). Additionally, a version scan was conducted, so there is now a “version” column which lists the actual service running on the port as opposed to the “service” column which just lists what is commonly on that port. Additionally, a default script scan has been executed.
That’s it!
Read More
PrivEsc: Token Impersonation with Incognito
Incognito is a tool which can be used for privilege escalation, typically from Local Administrator to Domain Administrator. It achieves this by allowing for token impersonation. As a local administrator can read the entirety of memory, if a domain administrator is logged in their authentication token can be stolen. We’ll [...]| Play | Cover | Release Label |
Track Title Track Authors |
|---|
