Penetration Testing
Web Applications
Web Application Penetration Tests are human-led, scope-limited engagements that aim to find vulnerabilities within web applications and application programming interfaces (APIs). These assessments will give an organisation a thorough understanding of the risk posed by their applications as well as detailed remediation guidance to ensure that the highlighted issues can be addressed and that systems can be hardened against any potential attack.
With many companies now relying heavily on web and mobile applications the impact of a security vulnerability in one of these systems can be devastating. We offer testing for web applications, covering everything from simple brochure websites to complex web applications and Application Programming Interfaces (API). This service is ideal for organisations that are worried about the exposure of their web applications to risks such as website defacement and data theft.
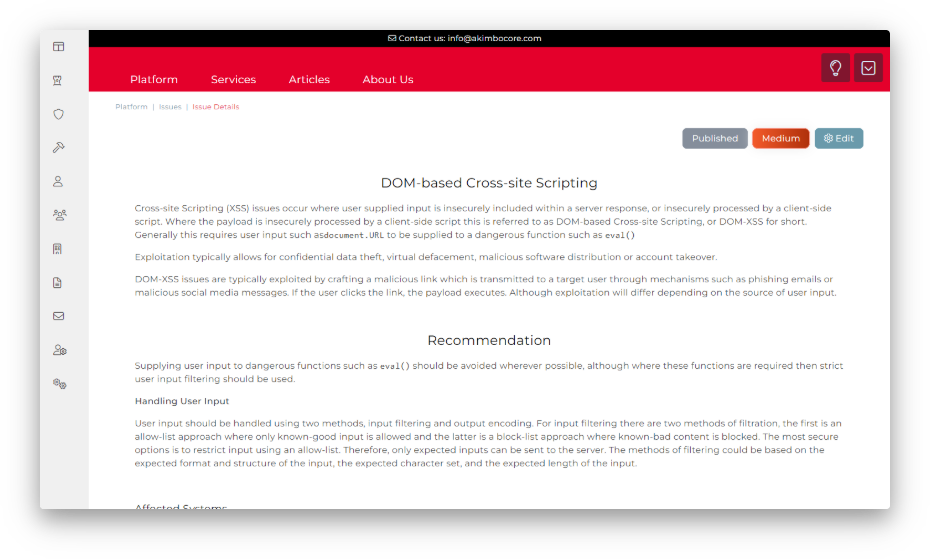
We don’t just focus on vulnerability discovery, but we also give significant detail on remediating discovered issues and importantly, hardening systems against exploitation. During the engagement you can track the findings within our web platform, allowing you to follow how the test is progressing but also to get a head start on remediating discovered issues. Once the assessment is complete, we will deliver a detailed report of findings and remediation guidance, as a record of your assessment.

Application Mapping
We will review the full attack surface before continuing onto the security assessment, ensuring that we achieve both depth and scope coverage. This can include reviewing the assessment scope to ensure that no assets have been unintentionally missed from the assessment scope.
Analysis and Exploitation
Where a vulnerability is discovered our testing report will include a full breakdown of the potential for exploitation thereby removing false positives, removing the guess work from grading vulnerability risks, and giving the steps to replicate the vulnerability to ensure that your technical teams fully understand each issue.
Underlying Infrastructure Assessment
Where requested we can include the underlying external infrastructure within a Web Application Assessment. Whilst most web servers only expose HTTP(S) to the internet we can review the system to ensure no additional services are exposed as well as ensuring that the cryptographic configuration of Transport Layer Security (TLS) is appropriate for the company.
Remediation
We don’t just focus on vulnerability discovery, but we also give significant detail on remediating discovered vulnerabilities and importantly, hardening systems against exploitation.
Application Vulnerability Discovery
We review the application for the presence of a range of vulnerabilities, including but not limited to those covered by awareness documents such as the OWASP Top 10. The following list gives an indication of the types of vulnerability that can be discovered through this type of engagement:
- Business logic issues
- Broken access control
- Cryptographic failures
- Injection vulnerabilities
- Insecure design
- Security misconfiguration
- Vulnerable or outdated components
- Identification and authentication failures
- Software and data integrity failures
- Security logging failures
- Server-side request forgery
- Cross-site request forgery
- Unvalidated redirects
- Weak account restrictions
- Insure file handling

In addition to Penetration Testing we also offer Cybersecurity Training and Cybersecurity Consultancy to offer a comprehensive suite of cybersecurity services.
Cybersecurity Training
Akimbo Core deliver cybersecurity workshops all around the UK, as well as remotely. Our workshops cover a range of topics from technical subjects such as how to get the most out of cybersecurity testing, to security awareness issues within businesses.

Cybersecurity Consultancy
From security architecture to security assessment, we offer a wide range of services to ensure the protection of your assets. We use a highly flexible methodology to ensure that our services are fully aligned to your needs, delivered by a bespoke team with the precise skills and depth of experience needed to understand your issues and then effectively deliver the desired outcome. With our security assurance services, you can have peace of mind knowing that your systems and data are well-protected.
CONTACT US

WE CAN FIND YOUR VULNERABILITIES
BEFORE YOU ARE BREACHED
GET IN TOUCH
© 2024 Akimbo Core Ltd
| Play | Cover | Release Label |
Track Title Track Authors |
Page | Buy | Delete |
|---|