Penetration Testing
cloud security
Akimbo’s Cloud Security Assessments will review the security stance of your cloud hosted systems. This can include the externally facing cloud-hosted infrastructure as well as the configuration on the Cloud Console. Our Cloud Security Assessments take into account vendor hardening guidelines, Industry Best Practices, as well as our own consultants experience performing a broad range of security assessments against organisations, ensuring that all major categories of security issue are considered.
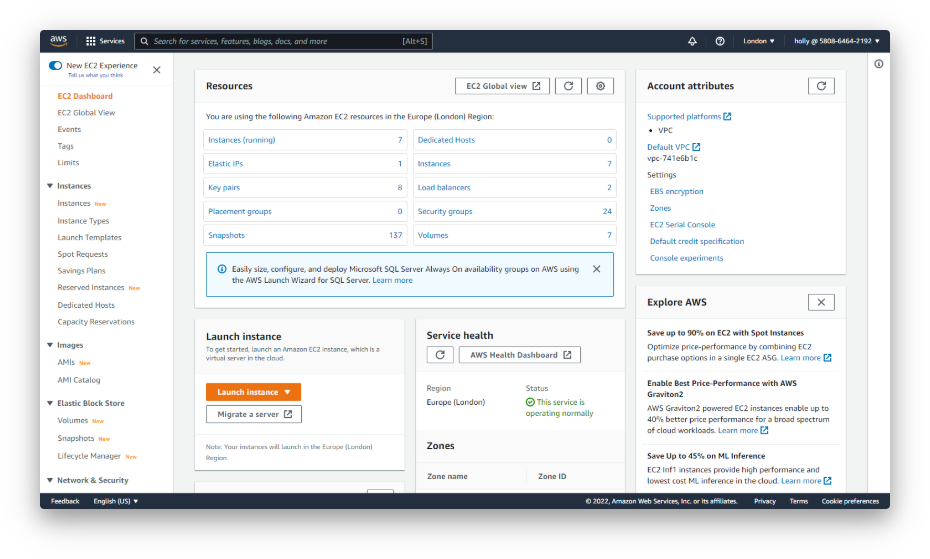
With so many companies moving workloads to major cloud platforms such as Azure and AWS, it’s important to keep on top of your cloud security.
We offer cybersecurity testing against cloud hosted applications, infrastructure, as well as assessing the configuration of your cloud console.

Security Testing Methodology Summary
Identity and Access Management (IAM)
We review the IAM configuration for a range of account management weaknesses, such as orphaned accounts, lack of multi-factor authentication, excessive permissions, lack of account lockout, and lack of enforced password policy.
Network Security
We review any access control lists that are in place, at a subnet level as well as an instance level, such as access control lists and security groups. This review will ensure that access restrictions are in place as well as ensuring that access control lists are not overly permissive.
Virtual Machines
We review virtual machines to ensure that any attached data-storage is appropriately encrypted and that access to servers is restricted where possible. Additionally, we ensure that access to any service is encrypted in-transit using secure mechanisms such as Transport Layer Security.
Storage
Cloud storage offers a great deal of flexibility but has its own considerations from a security point of view. We will review services such as AWS S3 and Azure Storage to ensure things such as access restrictions are in place and that encryption is used.
Logging and Monitoring
We review logging options to ensure that events are appropriately logged from all critical aspects of the cloud environment to ensure that an effective incident response capability would be possible.
Key Management
Ensuring that Key Management services such as Azure Key Vault and AWS Key Management are hardened, that backups are taken, that logging is enabled, and that recovery options are enabled.
Testing cloud infrastructure and web applications is similar in theory to testing on-prem hosted systems, although there are some key differences, such as the security of AWS instance metadata and the impact that cloud native features such as serverless computer can have.

In addition to Penetration Testing we also offer Cybersecurity Training and Cybersecurity Consultancy to offer a comprehensive suite of cybersecurity services.
Cybersecurity Training
Akimbo Core deliver cybersecurity workshops all around the UK, as well as remotely. Our workshops cover a range of topics from technical subjects such as how to get the most out of cybersecurity testing, to security awareness issues within businesses.

Cybersecurity Consultancy
From security architecture to security assessment, we offer a wide range of services to ensure the protection of your assets. We use a highly flexible methodology to ensure that our services are fully aligned to your needs, delivered by a bespoke team with the precise skills and depth of experience needed to understand your issues and then effectively deliver the desired outcome. With our security assurance services, you can have peace of mind knowing that your systems and data are well-protected.
CONTACT US

WE CAN FIND YOUR VULNERABILITIES
BEFORE YOU ARE BREACHED
GET IN TOUCH
© 2024 Akimbo Core Ltd
| Play | Cover | Release Label |
Track Title Track Authors |
Page | Buy | Delete |
|---|