Heya! I wrote this article back in mid-2020 for Ubuntu 18.04; it’s now the future and that’s an old version and no longer supported after April 30, 2023. If you’re looking for an updated copy of this article you can find it here: Hashcracking with Hashcat and AWS
Password cracking is a common step during compromising networks, from cracking wireless networks to compromising user passwords captured when LLMNR spoofing. In a previous post, I showed the steps to capture a WPA handshake and crack it using Hashcat. On my tiny travel laptop I achieved 416 hashes per second, which is…slow. AWS offers “GPU Optimized” EC2 instances which can offer a significant speed increase.
In this post we’ll run through setting up Hashcat on an AWS instance to allow for rapid password cracking. These instances are pricey, but you often only need to run them for short bursts. Example prices at the time of writing are:
- g4dn.xlarge – $0.53 per hour
- g3s.xlarge – $0.75 per hour
- p3.16xlarge – $24.48 per hour (that’s ~$18,000 per month!)
Whichever your budget allows, the setup is the same – except the p3.16xlarge will require a service limit increase on the AWS console.
GPU Instance Setup
1. Select a “Ubuntu Server 16.04 LTS (HVM), SSD Volume Type” AMI or a “Ubuntu Server 18.04 LTS (HVM), SSD Volume Type”. I’ll be using 18.04 here but I’ve used Hashcat on both.
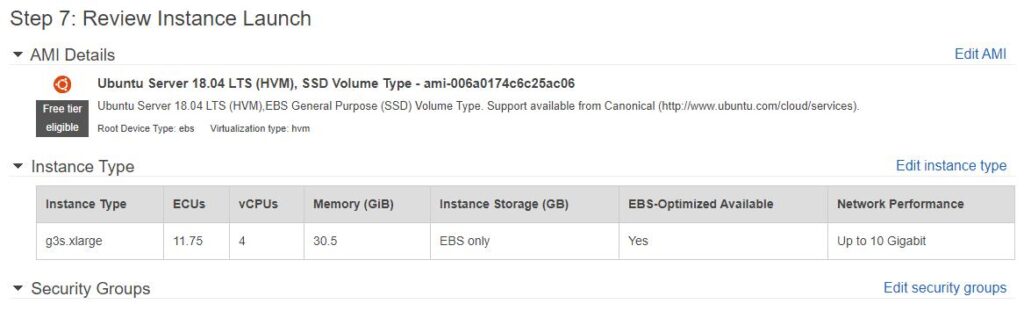
An example instance setup, using a g3s.xlarge
2. Update the system and install the necessary packages:
sudo apt-get update
sudo apt-get install -y linux-image-extra-virtual build-essential linux-headers-$(uname -r) p7zip-full3. Once you’re logged in to your new instance, add the following lines to /etc/modprobe.d/blacklist-nouveau.conf:
blacklist nouveau blacklist lbm-nouveau
options nouveau modeset=0
alias nouveau off
alias lbm-nouveau off4. Add the following to /etc/modprobe.d/nouveau-kms.conf:
options nouveau modeset=05. Update the boot process and reboot:
sudo update-initramfs -u
sudo reboot6. Download and install the NVIDIA package:
wget http://us.download.nvidia.com/tesla/440.33.01/NVIDIA-Linux-x86_64-440.33.01.run
sudo /bin/bash NVIDIA-Linux-x86_64-440.33.01.run --ui=none --no-questions --silent -X7. Test the installation:sudo nvidia-smi
This command shows that the drivers are working, and which card is currently in use. Here’s what it looks like on the smaller instances:
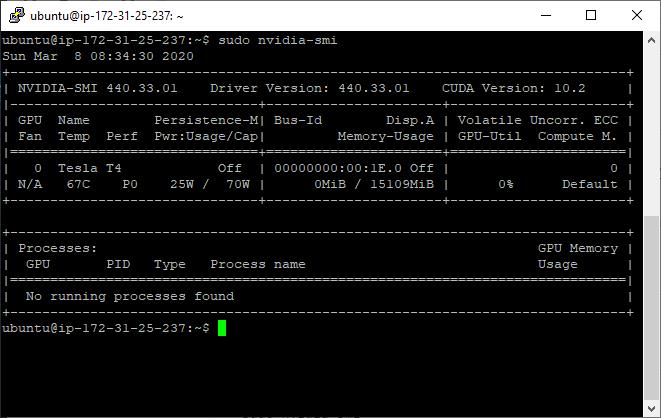
NVidia-smi running on Ubuntu 18.04, on a g4dn.xlarge
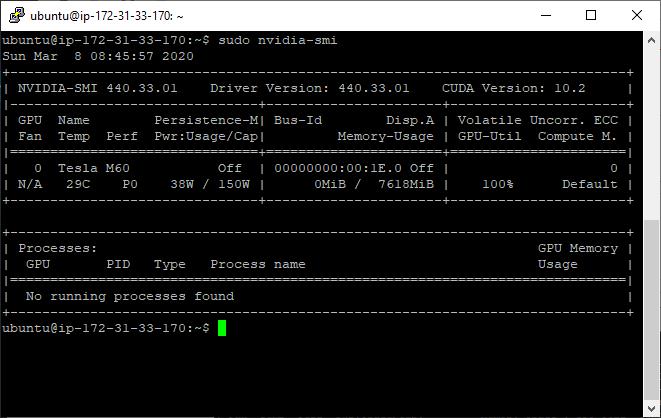
NVidia-smi running on Ubuntu 18.04 on a g3s.xlarge8.
Download and extract Hashcat:
wget https://hashcat.net/files/hashcat-5.1.0.7z
7za x hashcat-5.1.0.7zAt this stage you can run a benchmark to test everything is working. Here’s the benchmarks for the smaller instance types:
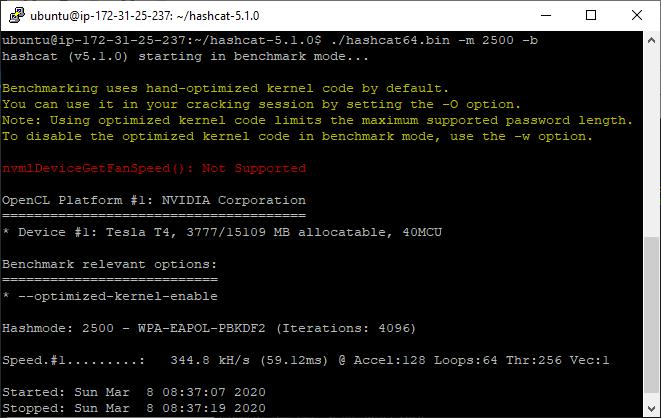
Hashcat WPA PSK Benchmark on Ubuntu 18.04, on a g4dn.xlarge – 344.8KH/s
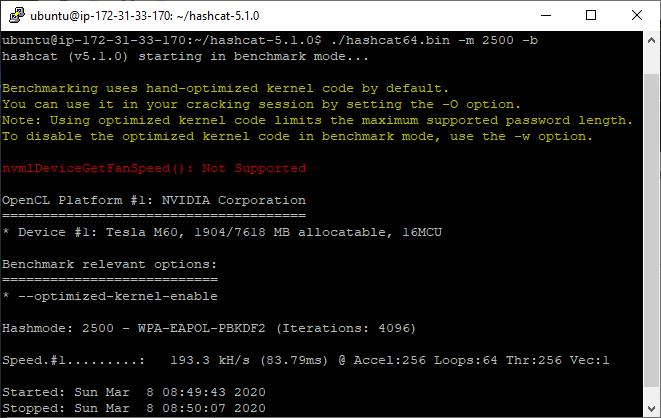
Hashcat WPA PSK Benchmark on Ubuntu 18.04, on a g3s.xlarge – 193.3KH/s
Now you can supply the hash to Hashcat and start cracking hashes! If you’ve captured a wireless hash with aircrack we discussed how to format it for Hashcat in a previous post.
A Bigger Boat
344.8 KH/s is pretty quick. However, as we mentioned at the top of the post if you increase your vCPU limit through a support request you can get access to p3.16xlarge instances. These instances are fast.
Building these instances follows exactly the same steps as previously mentioned, however the benchmark results are significantly higher. To highlight how powerful these instances are, here’s a side-by-side with my laptop, an i5-6500U running a Kali VM, next to a p3.16xlarge:
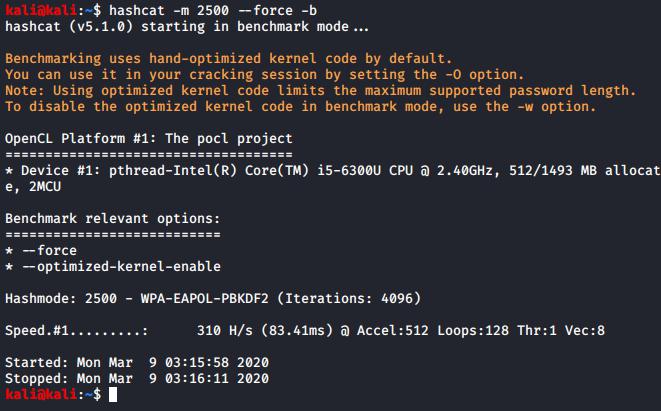
A VM running on an i5 benchmarking at: 310H/s
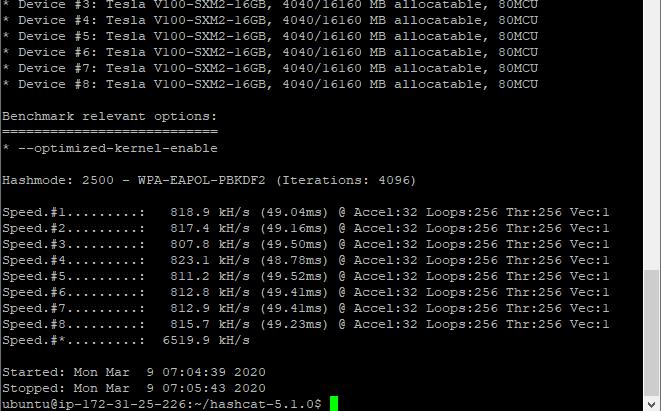
A p3.16xlarge instance benchmarking at: 6,519,900H/s
Results for WPA-EAPOL-PBKDF2 hashes:
g3s.xlarge: 193.3KH/s
g4dn.xlarge: 344.8KH/s
p3.16xlarge: 6519.9 KH/sThis shows that the p3.16xlarge instances are incredibly quick; for the curious a full benchmark of the p3.16xlarge is below:
0 - MD5 - 425.0 GH/s
100 - SHA1 - 142.8 GH/s
1400 - SHA2-256 - 60925.7 MH/s
1700 - SHA2-512 - 18995.9 MH/s
2500 - WPA-EAPOL-PBKDF2 - 6514.3 kH/s
1000 - NTLM - 680.2 GH/s
3000 - LM - 371.1 GH/s
5500 - NetNTLMv1 / NetNTLMv1+ESS - 417.6 GH/s
5600 - NetNTLMv2 - 31106.0 MH/s
1500 - descrypt, DES (Unix), Traditional DES - 15021.2 MH/s
500 - md5crypt, MD5 (Unix), Cisco-IOS $1$ (MD5) - 129.7 MH/s
3200 - bcrypt $2*$, Blowfish (Unix) - 433.4 kH/s
1800 - sha512crypt $6$, SHA512 (Unix) - 2920.8 kH/s
7500 - Kerberos 5 AS-REQ Pre-Auth etype 23 - 8177.1 MH/s
13100 - Kerberos 5 TGS-REP etype 23 - 7993.5 MH/s
15300 - DPAPI masterkey file v1 - 1156.7 kH/s
15900 - DPAPI masterkey file v2 - 961.4 kH/s
7100 - macOS v10.8+ (PBKDF2-SHA512) - 216.2 kH/s
11600 - 7-Zip - 158.2 kH/s
12500 - RAR3-hp - 842.8 kH/s
13000 - RAR5 - 707.6 kH/s
6211 - TrueCrypt - 4825.3 kH/s
13400 - KeePass 1 and KeePass 2 - 2645.3 kH/s
6800 - LastPass + LastPass sniffed - 40336.6 kH/s
11300 - Bitcoin/Litecoin wallet.dat - 85976 H/sThat’s it!
Read More
Using Metasploit
Metasploit is an exploitation framework. It’s a core tool of the penetration tester’s toolset and we use it for several of our vulnerability demonstrations, so it makes sense to write a quick “introduction to” for Metasploit. We’re going to look at the module system, navigating around, setting variables and running [...]| Play | Cover | Release Label |
Track Title Track Authors |
|---|
