In a previous article we discussed how bruteforcing Windows accounts is often easier than people expect. In this post – we’ll cover some steps to harden these accounts.
The Observation Window
When configuring an account lockout threshold on a Domain another setting is suggested, the observation window. This setting effectively reduces the protection of the account lockout by setting a timer. For example, a lockout threshold of 5 and an observation window of 30 minutes has the impact of meaning that if a threat actor attempts 5 incorrect passwords within 30 minutes the account will lock – but four passwords would not cause it to lock.
Therefore, an attacker could attempt 4 passwords every 30 minutes – or 192 per account per day, without locking any accounts.
This setting can be modified within Group Policy:
Computer Configuration → Windows Settings → Security Settings → Account Policies → Account Lockout Policy
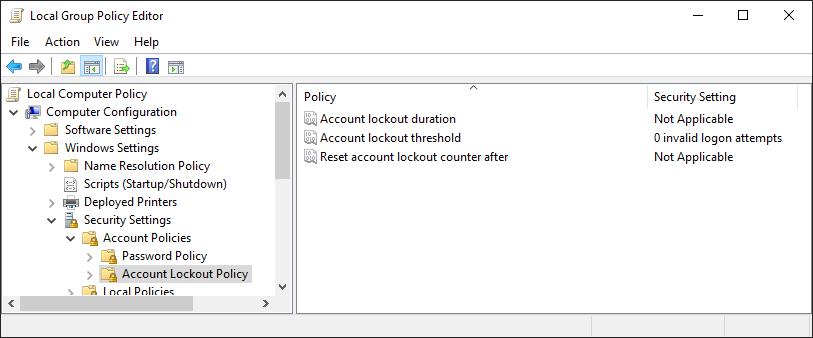
Within this menu there are three options:
- Account lockout duration: this timer controls how long an account will be locked for when the threshold is hit. A higher number will offer better security but will impact users when their accounts are locked.
- Account lockout threshold: this controls how many invalid passwords can be entered before an account is locked out.
- Reset account lockout counter after: this is the observation window, it controls how long before the lockout counter is reset; a higher figure will reduce the number of passwords an attacker could try per day. We recommend that the counter is set to a very high figure, such as 1440 (24 hours, in minutes) to mitigate the bruteforce attack described in our Bruteforcing Windows Accounts article.
Secure Passwords
When performing security tests, we very often come across weak passwords. We often see dictionary words with suffixes such as Welcome1, Password123, or Lockdown2020. We also see “leet” substitutions, such as P@55w0rd, 3l3ph@nt, or L0ckd0wn.
The options above are clearly not great so, we give details on more secure options in our Secure Passwords article.
Multi-factor Authentication
The most effective way to mitigate the risk of weak or compromised passwords is through the use of multi-factor authentication. Typically, two separate factors should be used. To be clear, using two of the same type of factor (often known as “two step authentication”) such as a password and a “secret work” is not as secure.
Factors include:
- Something you know: such as a password, pin number, or knowledge-based question
- Something you have: such as a smartcard or physical security token.
- Something you are: biometrics including fingerprints and face-scans.
The security of each factor is not the same; for example, knowledge-based questions such as “What is your Mother’s Maiden name?” are far more likely to be broken through open source intelligence gathering or simply guessing. Factors such as tokens sent via SMS may be compromised through SIM-swapping attacks or through interception. Therefore, physical security device such as U2F or mobile application in-app tokens are recommended instead.
That’s it!
Read More
Strong Passwords: Three Random Words
When performing security tests, we very often come across weak passwords. We often see dictionary words with suffixes such as Welcome1, Password123, or Lockdown2020. We also see “leet” substitutions, such as P@55w0rd, 3l3ph@nt, or L0ckd0wn. We’ve previously shown how quickly password cracking can be performed. With passwords like the above they [...]| Play | Cover | Release Label |
Track Title Track Authors |
|---|
